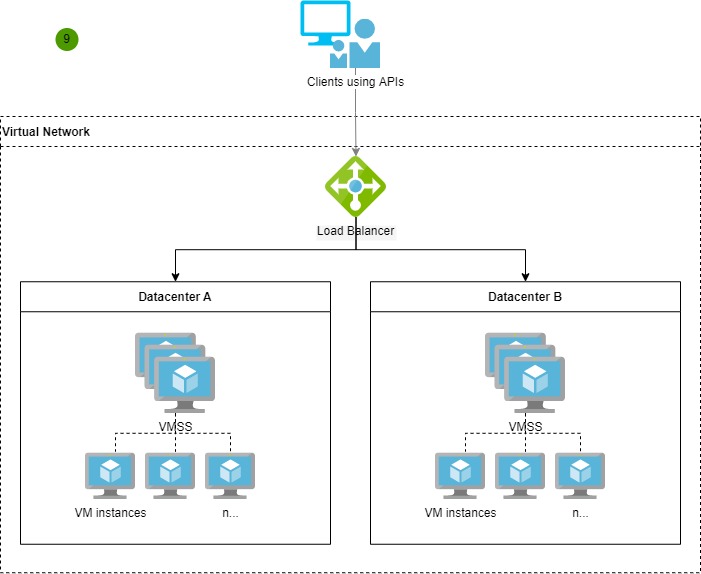
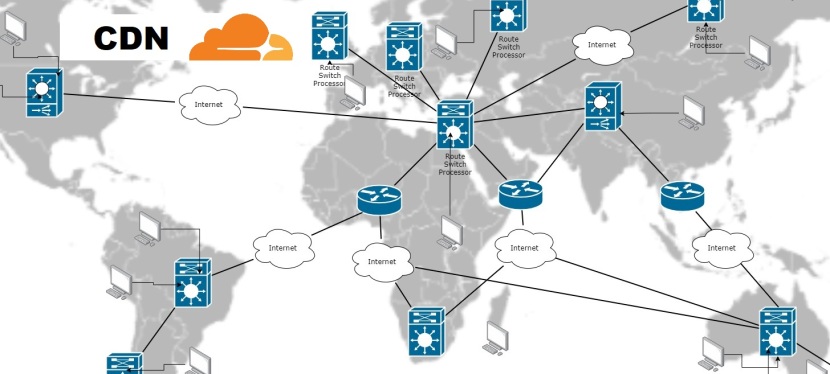
When I first delved into Rust, it felt like stepping into a world where safety, performance, and developer experience converge in harmony. As someone who’s often wrestled with the complexities of memory management, runtime bugs, and performance bottlenecks in other languages, Rust has been a game-changer. It has not only helped me reduce running costs for applications but also significantly improved their security and stability.
Let me take you on a journey through what makes Rust truly stand out, chapter by chapter, highlighting its most powerful features.
Zero-Cost Abstractions: Performance Without Sacrifice
One of Rust’s most impressive features is its zero-cost abstractions. High-level constructs like iterators and smart pointers provide clarity and elegance to your code but with zero performance overhead. This means you get the power of abstraction without sacrificing efficiency—a dream come true for anyone managing resource-heavy applications.
For me, this has translated into writing expressive code that’s both readable and as efficient as handcrafted low-level implementations. Rust makes me feel like I’m coding with superpowers, optimizing applications without even breaking a sweat.
[RUST]
fn main() {
let numbers = vec![1, 2, 3, 4, 5];
let doubled: Vec<i32> = numbers.iter().map(|x| x * 2).collect();
println!("{:?}", doubled); // Output: [2, 4, 6, 8, 10]
}This example demonstrates how Rust’s iterators provide high-level abstraction for traversing and transforming collections without performance overhead.
Ownership Model: Memory Safety Reinvented
Rust’s ownership model was a revelation for me. It ensures every value has a single owner, and once that owner goes out of scope, the memory is freed—no garbage collector, no fuss.
This elegant approach eliminates bugs like dangling pointers, double frees, and memory leaks. For anyone who’s spent late nights debugging memory issues (like I have), Rust feels like the safety net you didn’t know you needed. It’s not just about reducing bugs; it’s about coding with peace of mind.
[RUST]
fn main() {
let s = String::from("hello"); // s owns the memory
let s1 = s; // Ownership is transferred to s1
// println!("{}", s); // Uncommenting this line causes a compile error
println!("{}", s1); // Correct, as s1 now owns the memory
}
This shows how Rust ensures memory safety by transferring ownership, preventing use-after-free errors.
Borrowing Rules: Sharing Done Right
Building on the ownership model, Rust introduces borrowing rules, allowing you to share data through references without taking ownership. But there’s a catch (a good one): Rust enforces strict rules around lifetimes and mutability, ensuring your references never outlive the data they point to.
This might sound restrictive at first, but trust me—it’s liberating. Rust helps you avoid data races and other concurrency nightmares, making multi-threaded programming surprisingly smooth.
[RUST]
fn main() {
let mut x = 10;
{
let r1 = &x; // Immutable borrow
println!("r1: {}", r1);
// let r2 = &mut x; // Uncommenting this line causes a compile error
}
let r3 = &mut x; // Mutable borrow after immutable borrow scope ends
*r3 += 1;
println!("x: {}", x);
}
This code highlights borrowing rules, showcasing how Rust prevents data races by enforcing strict borrowing lifetimes.
Algebraic Data Types (ADTs): Expressive and Error-Free
Rust’s Algebraic Data Types (ADTs) are like a Swiss Army knife for designing robust data models. Whether it’s enums, structs, or tuples, Rust lets you express relationships concisely.
The Option and Result types are my personal favorites. They force you to handle errors explicitly, reducing those frustrating runtime surprises. Combined with pattern matching, Rust makes handling edge cases a breeze. ADTs in Rust don’t just make code cleaner—they make it safer.
[RUST]
fn divide(a: i32, b: i32) -> Option<i32> {
if b == 0 {
None
} else {
Some(a / b)
}
}
fn main() {
match divide(10, 2) {
Some(result) => println!("Result: {}", result),
None => println!("Cannot divide by zero!"),
}
}
Rust’s Option type ensures that edge cases like division by zero are handled explicitly, reducing runtime errors.
Polymorphism: Traits Over Classes
Rust’s approach to polymorphism is refreshingly different. Forget bloated inheritance hierarchies—Rust uses traits to define shared behavior across types. This static dispatch ensures zero runtime cost.
When I need flexibility, Rust also offers dynamic dispatch via dyn Trait. It’s the best of both worlds—flexibility where needed and performance everywhere else.
[RUST]
trait Area {
fn area(&self) -> f64;
}
struct Circle {
radius: f64,
}
struct Rectangle {
width: f64,
height: f64,
}
impl Area for Circle {
fn area(&self) -> f64 {
3.14 * self.radius * self.radius
}
}
impl Area for Rectangle {
fn area(&self) -> f64 {
self.width * self.height
}
}
fn print_area<T: Area>(shape: T) {
println!("Area: {}", shape.area());
}
fn main() {
let circle = Circle { radius: 5.0 };
let rectangle = Rectangle { width: 4.0, height: 3.0 };
print_area(circle);
print_area(rectangle);
}
This demonstrates Rust’s trait-based polymorphism, allowing shared behavior across different types.
Async Programming: Concurrency with Confidence
Rust’s async/await model is a masterpiece of design. Writing asynchronous code that feels synchronous is a joy, especially when you know Rust’s ownership rules are keeping your data safe.
For my high-throughput projects, Rust’s lightweight async tasks have been a game-changer. I’ve seen noticeable improvements in scalability and responsiveness, proving Rust isn’t just about safety—it’s about speed, too.
[RUST]
use tokio::time::{sleep, Duration};
#[tokio::main]
async fn main() {
let task1 = async_task(1);
let task2 = async_task(2);
tokio::join!(task1, task2);
}
async fn async_task(id: u32) {
println!("Task {} started", id);
sleep(Duration::from_secs(2)).await;
println!("Task {} completed", id);
}
Using the Tokio runtime, Rust enables asynchronous programming with minimal overhead, ideal for scalable applications.
Meta Programming: Automate the Boring Stuff
Rust’s support for meta-programming is a lifesaver. With procedural macros and attributes, Rust automates repetitive tasks elegantly.
One standout for me has been the serde library, which uses macros to simplify serialization and deserialization. It’s like having an extra pair of hands, ensuring you can focus on logic rather than boilerplate.
Macros: Power and Simplicity
Rust’s macros are not just about simple text replacement; they’re a gateway to reusable, efficient patterns. Whether it’s creating custom DSLs or avoiding code duplication, macros have saved me countless hours.
What I love most is how declarative macros make the complex simple, ensuring my codebase remains DRY (Don’t Repeat Yourself) without becoming cryptic.
[RUST]
macro_rules! say_hello {
() => {
println!("Hello, Rustaceans!");
};
}
fn main() {
say_hello!(); // Expands to: println!("Hello, Rustaceans!");
}
Rust’s macros simplify repetitive code, boosting productivity without runtime costs.
Cargo: Your New Best Friend
Managing dependencies and builds can often feel like a chore, but Rust’s Cargo turns it into a seamless experience. From managing dependencies to building projects and running tests, Cargo is the all-in-one tool I never knew I needed.
I particularly appreciate its integration with crates.io, Rust’s package registry. Finding and using libraries is intuitive and hassle-free, leaving me more time to focus on building features.
[RUST]
[dependencies]
tokio = { version = "1.0", features = ["full"] }
serde = { version = "1.0", features = ["derive"] }
With Cargo, adding dependencies is as simple as updating the Cargo.toml file. Here, tokio is used for asynchronous programming and serde for data serialization.
Why I’m Sticking with Rust
Rust has redefined what I expect from a programming language. Its combination of safety, performance, and developer-friendly tools has allowed me to build applications that are not only faster and more secure but also more cost-efficient.
If you’re still unsure whether Rust is worth the learning curve, let me leave you with this: Rust isn’t just a language—it’s a way to write code you can be proud of. It’s about building software that stands the test of time, with fewer bugs and better resource efficiency.
Here’s to building the future—one safe, efficient, and high-performance Rust program at a time. 🚀
Highlighted Features in Summary: Wrap-up
- Zero-Cost Abstractions: Write expressive code without runtime overhead.
- Ownership Model: Memory safety without garbage collection.
- Borrowing Rules: No data races; safe and efficient memory sharing.
- Algebraic Data Types (ADTs): Cleaner, safer error handling.
- Polymorphism: Trait-based, with no runtime cost.
- Async Programming: Lightweight, high-performance concurrency.
- Meta Programming: Automate repetitive tasks effortlessly.
- Macros: Powerful and reusable patterns.
- Cargo: The all-in-one tool for dependency and project management.
If this resonates with your development goals or sparks curiosity, give Rust a try—you won’t regret it!

Thanks again for returning to my blog!
Sources used for this article:
https://www.rust-lang.org/
https://doc.rust-lang.org/stable/